CMMC and FedRamp are two of the compliance regimes every Defense contractor needs to be familiar with. In today’s post, we take a detailed look at the difference in scope, characteristics, and goals between these two frameworks. Keep reading to learn more.
What Is CMMC?
CMMC stands for Cybersecurity Maturity Model Certification, a three-tier cybersecurity model geared towards protecting Controlled Unclassified Information throughout the Defense Industrial Base (DIB).
Each CMMC level builds upon the previous one, prescribing an increasingly complex set of cybersecurity practices:
- Level 1, Foundational (17 practices)
- Level 2, Advanced (110 practices)
- Level 3, Expert (110+ practices)
If you want to learn more about CMMC, be sure to read our previous blogs:
What Is FedRAMP?
FedRAMP is short for Federal Risk and Authorization Management Program, an initiative by the U.S. government that promotes the adoption of secure cloud services across the federal government.
Cloud services are resources that reside on the internet, providing on-demand access from anywhere around the world to configurable assets such as networks, servers, storage, or applications.
Some examples of cloud services you may be familiar with as a Defense contractor include Microsoft GCC High and Microsoft DoD.
No doubt, cloud services can improve the efficiency of any organization thanks to their convenience and wide availability. However, cloud computing also poses unique cybersecurity challenges. Needless to say, the stakes are even higher when sensitive government information is involved.
Here’s where FedRAMP comes into play. FedRAMP provides a standardized way to approach and assess three basic aspects of cloud products and services:
- Security assessment
- Authorization
- Continuous monitoring
The FedRAMP model divides Cloud Service Offerings (CSO) into three impact levels:
- Low (125 controls). Appropriate for CSOs where the loss of confidentiality, integrity, and availability would have only limited adverse effects.
- Moderate (325 controls). For CSOs where the loss of confidentiality, integrity, and availability would result in serious adverse effects.
- High (421 controls). For any system where loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect.
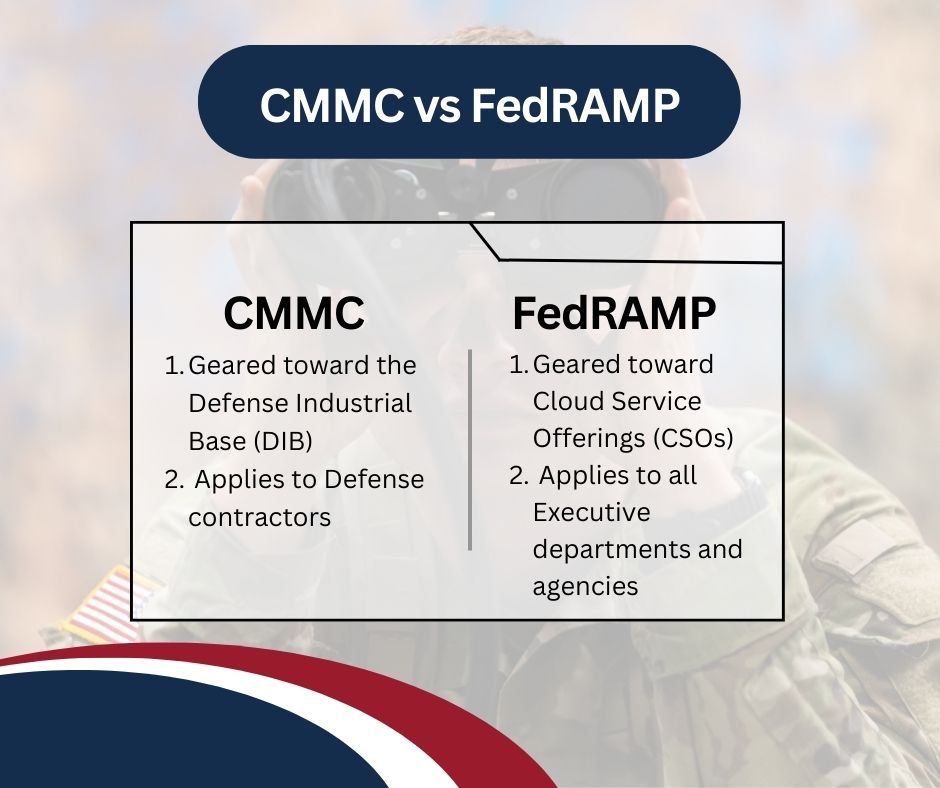
CMMC vs FedRAMP
The basic difference between CMMC and FedRAMP is that while the Cybersecurity Maturity Model Certification aims to ensure that Controlled Unclassified Information (CUI) is handled securely, FedRAMP focuses on Cloud Service Offerings.
Another important difference is that while CMMC was designed with Defense contractors in mind, FedRAMP applies to all Executive departments and agencies (a list that includes not only DoD but also the Department of Agriculture, the Department of Commerce, and the Department of Energy, among others).
Contact our CMMC Registered Practitioners Today
It is important to remember that since the main purpose of CMMC is to assess a contractor’s implementation of certain cybersecurity practices, there’s no CMMC certification for cloud services.
Instead, CMMC refers to FedRAMP when it comes to cloud offerings. For example, according to the official CMMC FAQ, companies can use commercial instances of cloud offerings as long as the cloud offering meets the security requirements equivalent to the FedRAMP Moderate baseline and as long as the provider meets the requirements of paragraphs (c)-(g) of DFARS 252.204-7012 (b)(ii)(D). These requirements include:
- Cyber incident reporting. After a cyber incident that affects a covered information system, the contractor must conduct a review and rapidly report the incident to DoD.
- Malicious software. When a contractor identifies malicious software related to a reported cyber incident, it must submit the software to DoD Cyber Crime Center (DC3).
- Media preservation and protection. After a cyber incident, contractors must preserve images of affected systems and related monitoring/capture data for at least 90 days from the submission of the cyber incident report.
- Access to additional information or equipment necessary for forensic analysis. After a cyber incident, contractors must allow DoD access to all relevant data and/or hardware.
- Cyber Incident Damage Assessment activities. If DoD chooses to conduct a damage assessment after a cyber incident, the contracting officer will ask the contractor to provide all the damage assessment information gathered as part of point 3.
Need To Achieve CMMC Compliance? We Are Here To Help
Whether it’s CMMC, NIST SP 800-171, DFARS, or ITAR, we help organizations achieve compliance with all applicable cybersecurity regulations at any level so that they can win and maintain Department of Defense (DoD) contracts.
Brea Networks, LLC is a fully Registered Provider Organization (RPO) and is a Microsoft partner with full Microsoft GCC High licensing and migration solutions.
Contact our CMMC Registered Practitioners today by clicking here.
Brea Networks, LLC / CMMCCompliance.us
451 W. Lambert Rd Suite 214
Brea, CA 92821
Tel: (714) 592-0063
Photo source: media.defense.gov
Disclaimer: “The appearance of U.S. Department of Defense (DoD) visual information does not imply or constitute DoD endorsement.”