Many organizations looking to comply with the Cybersecurity Maturity Model Certification (CMMC) already observe other standards such as SOC 2. With that in mind, today we take a closer look at the similarities and differences between these two standards, including who needs to adhere to them and how to become certified.
What Is CMMC?
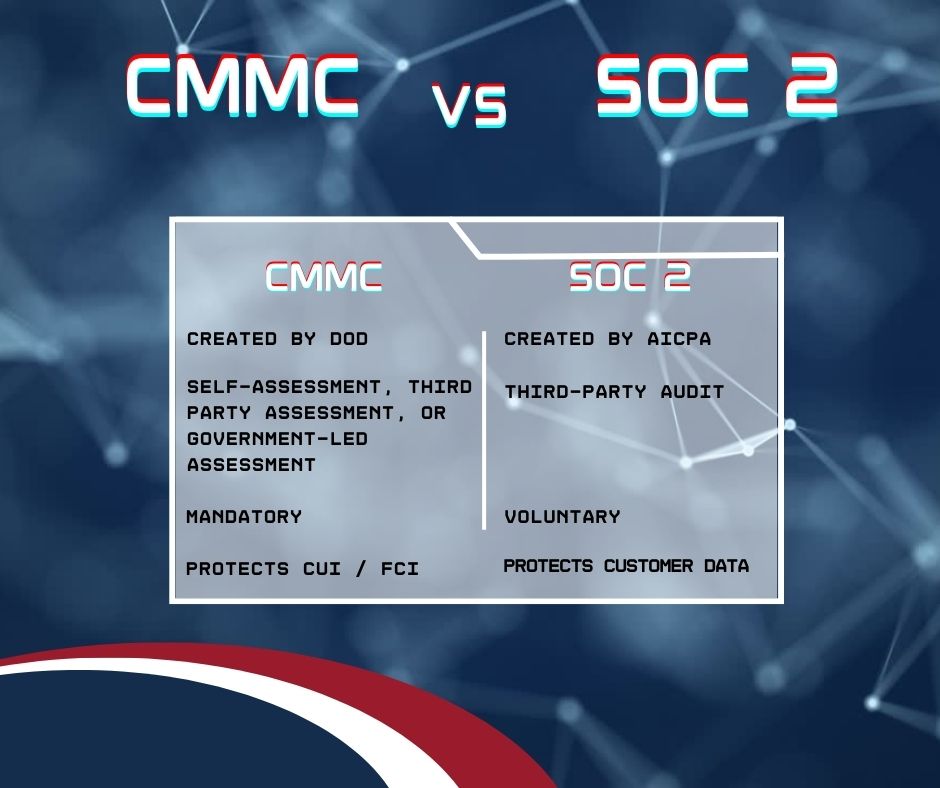
The Cybersecurity Maturity Model Certification (CMMC) is a certification program created by the Department of Defense (DoD) to enhance the cybersecurity posture of the Defense Industrial Base (DIB).
The CMMC model measures the maturity of a company’s cybersecurity processes and practices across three levels:
- Foundational: This level aligns with the requirements of Federal Acquisition Regulation (FAR) 52.204-21 and includes 17 basic cybersecurity controls.
- Advanced: This level aligns with the requirements of NIST SP 800-171 and includes 110 cybersecurity controls.
- Expert: Includes additional cybersecurity practices beyond NIST SP 800-171 for organizations that handle critical technologies or perform critical services.
All DoD contractors and subcontractors are subject to the CMMC certification program, and the level of certification required depends on the amount and type of sensitive data they handle.
To learn more about CMMC, read our previous blogs, “CMMC for Small Businesses: A Starter Kit” and “Why Is CMMC Important?”
What Is SOC 2?
SOC is a series of compliance standards developed by the American Institute of Certified Public Accountants (AICPA). SOC stands for “System and Organization Controls,” and the number 2 refers to the type of report.
A SOC 2 audit report focuses on a service organization’s non-financial reporting controls (SOC 1 deals with financial reporting) as they relate to security, availability, processing integrity, confidentiality, and privacy of a system.
These reports are designed to meet the needs of a broad range of users who need detailed information and assurance about the controls at a service organization relevant to security, availability, and processing integrity of the systems the service organization uses to process users’ data and the confidentiality and privacy of the information processed by these systems.
These reports are issued by independent third-party auditors who assess the extent to which a vendor complies with the five trust service principles:
- Security: The system is protected against unauthorized access.
- Availability: The system is available for operation and use as committed or agreed.
- Processing Integrity: System processing is complete, valid, accurate, timely, and authorized.
- Confidentiality: Information designated as confidential is protected.
- Privacy: Personal information is collected, used, retained, disclosed, and destroyed in conformity with the commitments in the entity’s privacy notice and with the criteria set forth in Generally Accepted Privacy Principles (GAPP) issued by the AICPA and CICA.
In short, a company that has achieved SOC 2 certification has proven its system is designed to keep sensitive customer data secure.
CMMC vs SOC 2
While there is some overlap between the Cybersecurity Maturity Model Certification and SOC 2, the differences outweigh the similarities.
To begin with, CMMC is geared toward the Defense Industrial Base, while SOC 2 is for any company looking to improve their data protection standards.
SOC 2 was designed to secure customer data. CMMC, on the other hand, safeguards Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
In order to obtain a SOC 2 attestation, companies must go through an audit by a third-party auditor. With CMMC, by contrast, the certification method will vary depending on the CMMC level a contractor wishes to be certified for (self-assessments for CMMC Level 1, third-party assessments for CMMC Level 2, and government-led assessments for CMMC Level 3).
Another important difference is that CMMC is mandatory for defense contractors and subcontractors, while SOC 2 is a voluntary program.
As for any acceptance agreements between CMMC and SOC 2, there is no official information available at present, although DoD has stated that it is “considering other standards acceptance, where appropriate, to satisfy CMMC requirements,” without specifying what other standards are being considered.
Need To Achieve CMMC Compliance? We Are Here To Help
Whether it’s CMMC, NIST SP 800-171, DFARS, or ITAR, we help organizations achieve compliance with all applicable cybersecurity regulations at any level so that they can win and maintain Department of Defense (DoD) contracts.
Brea Networks, LLC is a fully Registered Provider Organization (RPO) and is a Microsoft partner with full Microsoft GCC High licensing and migration solutions.
Contact our CMMC Registered Practitioners today by clicking here.
Brea Networks, LLC / CMMCCompliance.us
451 W. Lambert Rd Suite 214
Brea, CA 92821
Tel: (714) 592-0063




