As you try to make sense of the Cybersecurity Maturity Model Certification, you’ll come across all kinds of obscure technical terms. For example: What is FIPS-Validated Cryptography? What does it have to do with CMMC? Follow along to discover the answers.
What Is FIPS?
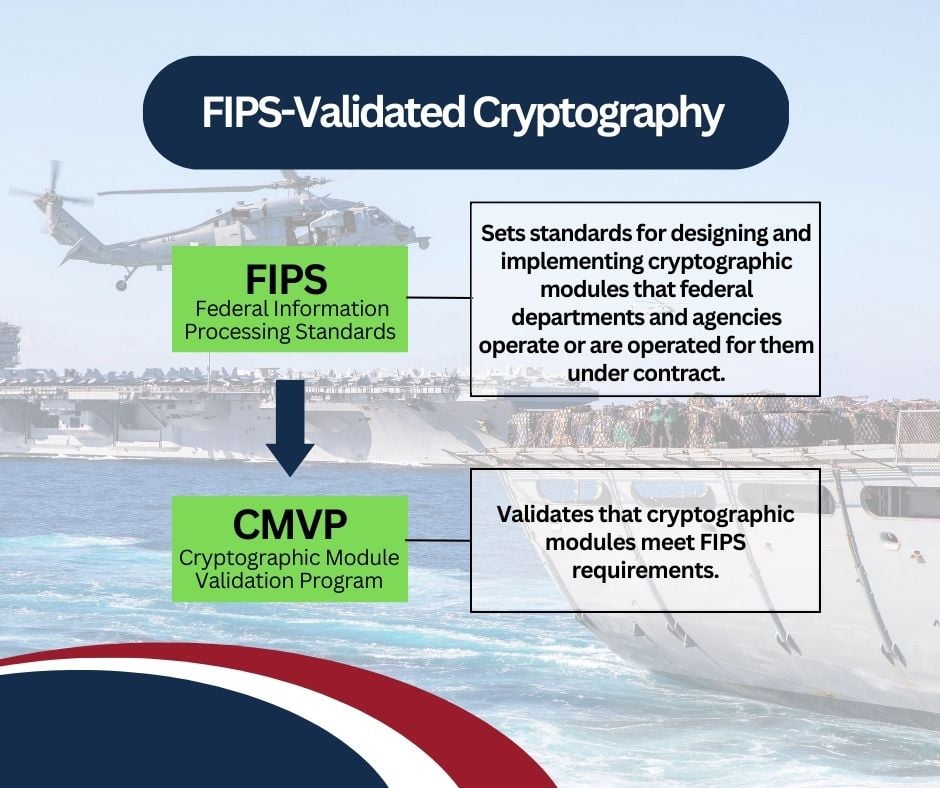
FIPS stands for Federal Information Processing Standards, a set of data security standards developed by the U.S. government to be used by non-military agencies or government contractors.
There are many different FIPS publications out there, with each one outlining standards for specific aspects of data security, such as:
- Personal Identity Verification (PIV)
- Digital signature standards
- Security requirements for federal information systems
FIPS Publication 140-2, “Security Requirements for Cryptographic Modules”, for example, deals with cryptography, defined as the use of mathematical techniques to prevent data from being read by unauthorized parties.
FIPS Publication 140-2 establishes four increasing levels of cryptographic security with specific technical requirements for a wide range of areas, including:
- Cryptographic module specification
- Cryptographic module ports and interfaces
- Roles, services, and authentication
- Finite state model
- Physical security
- Operational environment
- Cryptographic key management
- EMI/ENC
- Self-tests
- Design assurance
- Mitigation of other attacks
What Is FIPS-Validated Cryptography?
The term “FIPS-validated cryptography” refers to a cryptographic module validated to meet the technical requirements outlined by FIPS.
A cryptographic module, in turn, is the set of hardware and software that implements functions such as cryptographic algorithms and key generation methods.
So, for example, the term “cryptographic module” can refer to encryption software or to the physical circuitry a router (or other similar device) uses to encrypt data.
Cryptographic modules are validated to meet FIPS requirements by the Cryptographic Module Validation Program (CMVP), a joint effort between the National Institute of Standards and Technology (NIST) and the Canadian Centre for Cyber Security.
Note that as a prerequisite to CMVP validation, cryptographic modules are required to use a cryptographic algorithm that has successfully passed validation testing by the Cryptographic Algorithm Validation Program (CAVP).
dt_gap height=”20″ /]
Contact our CMMC Registered Practitioners Today
FIPS-Validated vs FIPS-Compliant
Adding to the confusion of defense contractors, some products or software are advertised as FIPS-validated while others are presented as FIPS-Compliant. What is the difference?
These are two different categories that are NOT interchangeable:
- FIPS-Validated products have undergone testing by an accredited national laboratory.
- FIPS-Compliant products contain FIPS-Validated components, although the product as a whole hasn’t received FIPS validation.
As we’ll see in greater detail in the next section, CMMC compliance entails using cryptographic products that are FIPS-validated.
You can use this search form to check if a module has received validation.
Here’s a list of the cryptographic modules whose CMVP validation is in process.
So What Does FIPS-Validated Cryptography Have To Do With CMMC?
FIPS-validated cryptography matters if you want to achieve CMMC compliance because the National Institute of Standards and Technology (and by extension the Cybersecurity Maturity Model Certification) sees non-validated cryptographic modules as providing NO data protection.
While CMMC Level 1 doesn’t include a FIPS validation requirement for cryptography, the practice “CUI Encryption” of CMMC Level 2 (under the domain “Systems and Communication Protection”) mandates to “Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.”
It makes sense: the main goal of CMMC is to protect Controlled Unclassified Information (CUI), and one of the most effective ways to protect any kind of data is by using cryptography.
And although all the above sounds straightforward enough, FIPS-validated cryptography is one of the aspects of CMMC compliance that causes more headaches among DoD contractors.
If you have questions about FIPS-validated cryptography or about any other area of CMMC compliance, don’t hesitate to contact our CMMC Registered Practitioners. We stand ready to offer assistance and answer all your questions.
Need To Achieve CMMC Compliance? We Are Here To Help
Whether it’s CMMC, NIST 800-171, DFARS, or ITAR, we help organizations achieve compliance with all applicable cybersecurity regulations at any level so that they can win and maintain Department of Defense (DoD) contracts.
Brea Networks, LLC is a fully Registered Provider Organization (RPO) and is a Microsoft partner with full Microsoft GCC High licensing and migration solutions.
Contact our CMMC Registered Practitioners today by clicking here.
Brea Networks, LLC / CMMC Compliance
451 W. Lambert Rd Suite 214
Brea, CA 92821
Tel: (714) 592-0063
Photo sources- Header: https://cmmccompliance.us/; graphic: @USArmy, link to license
Disclaimer: “The appearance of U.S. Department of Defense (DoD) visual information does not imply or constitute DoD endorsement.”




