If you are familiarizing yourself with the Cybersecurity Maturity Model Certification, chances are good that you have heard or read the term “CMMC Controls.” However, the official CMMC model doesn’t mention controls. So, what are CMMC controls, exactly? In today’s blog, we tell you everything you need to know.
About CMMC Controls
At its core, CMMC is a cybersecurity framework, and it’s common for cybersecurity frameworks to use the term “controls” to refer to mechanisms designed to help mitigate cyber threats. When talking about CMMC, some people keep using “controls” out of habit. However, the appropriate CMMC terminology is “practices.”
CMMC Practices
A CMMC practice is defined as an activity or set of activities that are performed to meet the defined CMMC objectives.
Each of the three levels of the Cybersecurity Maturity Model Certification prescribes a set number of practices organized as follows:
- CMMC Level 3: 110+ practices based on NIST SP 800-171 and 800-172
- CMMC Level 2: 110 practices aligned with NIST SP 800-171
- CMMC Level 1: 17 practices
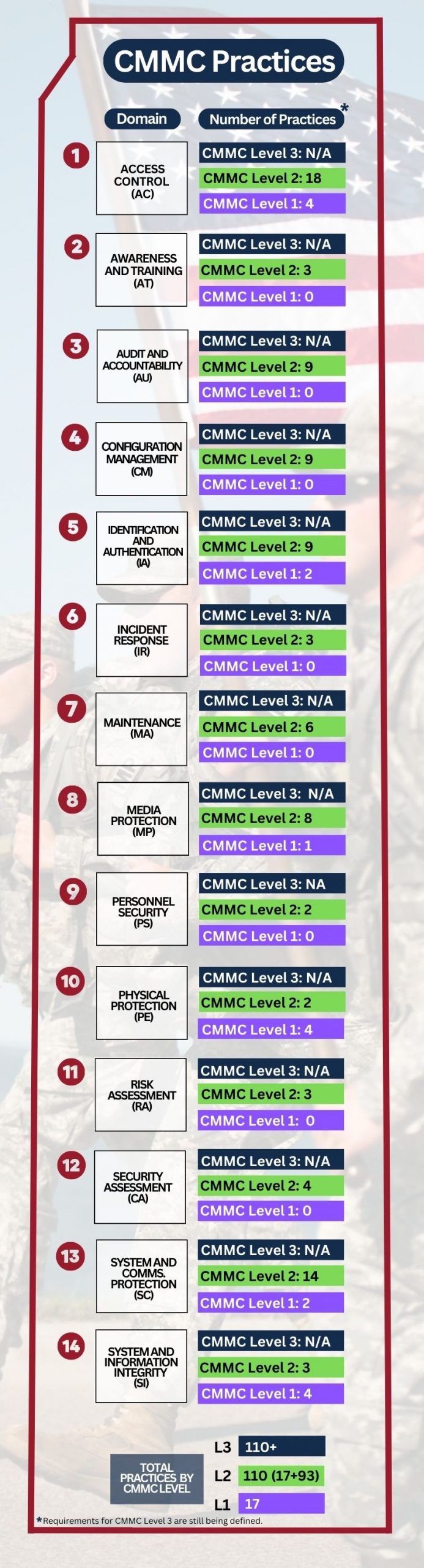
As you can see from the chart above, CMMC practices are grouped into 14 cybersecurity domains. To learn more about CMMC domains, just click on any domain below to jump to the corresponding section; there you’ll find a definition of each domain, as well as an example of the CMMC practices within that domain:
- Access Control (AC)
- Awareness and Training (AT)
- Audit and Accountability (AU)
- Configuration Management (CM)
- Identification and Authentication (IA)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PE)
- Risk Assessment (RA)
- Security Assessment (CA)
- System and Communications Protection (SC)
- System and Information Integrity (SI)
Each CMMC practice is associated with a combination of letters and numbers that convey the practice domain as well as the CMMC level the practice belongs to.
Take, for example, the practice “Authorized Access Control” (AC.L1-3.1.1). “AC” stands for the domain “Access Control,” while “L1” indicates that the practice is part of the requirements for CMMC Level 1.
Note, however, that CMMC levels build upon each other, so although in this example the practice “Authorized Access Control” is cataloged as belonging to CMMC Level 1, organizations aspiring to achieve CMMC Level 2 or CMMC Level 3 compliance must observe this practice too.
2. Awareness and Training (AT) Domain
The AT domain requires defense contractors to have systems and mechanisms in place within their organizations to explain proper rules of behavior for the use of agency information systems and information. An awareness and training program communicates information technology (IT) security policies and procedures that need to be followed.
Example of Awareness and Training Practices
Role-Based Risk Awareness (AT.L2-3.2.1): Ensure that managers, systems administrators, and users of organizational systems are made aware of the security risks associated with their activities and of the applicable policies, standards, and procedures related to the security of those systems.
3. Audit and Accountability (AU) Domain
In the context of CMMC, an audit is an independent review and examination of records and activities to assess the adequacy of system controls to ensure compliance with established policies and operational procedures, and recommend necessary changes in controls, policies, or procedures.
Accountability, on the other hand, is defined as the security goal that generates the requirement for the actions of an individual or institution to be traced uniquely to that individual or institution.
Example Audit and Accountability (AU) Practices
System Auditing (AU.L2-3.3.1): Create and retain system audit logs and records to the extent needed to enable the monitoring, analysis, investigation, and reporting of unlawful or unauthorized system activity.
4. Configuration Management (CM) Domain
The Configuration Management domain is a collection of activities focused on establishing and maintaining the integrity of information technology products and systems, through control of processes for initializing, changing, and monitoring the configurations of those products and systems throughout the system development life cycle.
Example of Configuration Management Practices
Security Configuration Enforcement (CM.L2-3.4.2): Establish and enforce security configuration settings for information technology products employed in organizational systems.
5. Identification and Authentication (IA) Domain
Identification is the process of discovering the true identity (i.e., origin, initial history) of a person or item from the entire collection of similar persons or items.
Authentication, for its part, is a security measure designed to protect a communications system against acceptance of fraudulent transmission or simulation by establishing the validity of a transmission, message, originator, or an individual’s eligibility to receive specific categories of information.
Example of Identification and Authentication Practices
Identifier Reuse (IA.L2-3.5.5): Prevent reuse of identifiers for a defined period.
6. Incident Response (IR) Domain
Refers to the actions an organization takes to prevent or contain the impact of a cybersecurity incident while the incident is occurring or shortly after it has occurred.
Example of Incident Response Practices
Incident Reporting (IR.L2-3.6.2): Track, document, and report incidents to designated officials and/or authorities both internal and external to the organization.
7. Maintenance (MA) Domain
This domain includes actions that either prevent the failure or malfunction of equipment or restore its operating capability.
Example of Maintenance Practices
Equipment Sanitization (MA.L2-3.7.3): Ensure equipment removed for off-site maintenance is sanitized of any CUI.
8. Media Protection (MP) Domain
Refers to the protection (i.e., physical control and secure storage) of system media containing CUI, both paper and digital.
Example of Media Protection Practices
Media Disposal (MP.L1-3.8.3): Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
9. Personnel Security (PS) Domain
Practices within this domain are geared towards ensuring that organizational systems containing CUI are protected during and after personnel actions, including terminations, transfers, and others
Example of Personnel Security Practices
Screen Individuals (PS.L2-3.9.1): Screen individuals prior to authorizing access to organizational systems containing CUI.
10. Physical Protection (PE) Domain
This domain covers practices whose aim is to ensure that physical access to CUI asset containers is strictly controlled, managed, and monitored in accordance with CUI protection requirements.
Example of Physical Protection Practices
Escort Visitors (PE.L1-3.10.3): Escort visitors and monitor visitor activity.
11. Risk Assessment (RA) Domain
This domain deals with the process of identifying risks to organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the Nation, resulting from the operation of a system.
Example of Risk Assessment Practices
Vulnerability Scan (RA.L2-3.11.2): Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified.
12. Security Assessment (CA) Domain
This domain refers to the testing or evaluation of security controls to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome.
Example of Security Assessment Practices
System Security Plan (CA.L2-3.12.4): Develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or connections to other systems.
13. System and Communications Protection (SC) Domain
System and Communications Protection practices ensure that an organization is actively identifying, managing, and controlling all system and communication channels that store or handle CUI.
Example of System and Communications Protection Practices
CUI Encryption (SC.L2-3.13.11): Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.
14. System and Information Integrity (SI) Domain
This domain consists of practices geared toward ensuring that technology assets containing CUI are continuously monitored to detect violations or other types of malicious activity.
Example of System and Information Integrity Practices
System & File Scanning (SI.L1-3.14.5): Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
Need To Achieve CMMC Compliance? We Are Here To Help
Whether it’s CMMC, NIST SP 800-171, DFARS, or ITAR, we help organizations achieve compliance with all applicable cybersecurity regulations at any level so that they can win and maintain Department of Defense (DoD) contracts.
Brea Networks, LLC is a fully Registered Provider Organization (RPO) and is a Microsoft partner with full Microsoft GCC High licensing and migration solutions.
Contact our CMMC Registered Practitioners today by clicking here.
Brea Networks, LLC / CMMCCompliance.us
451 W. Lambert Rd Suite 214
Brea, CA 92821
Tel: (714) 592-0063
Photo source: @USArmy, link to license
Disclaimer: “The appearance of U.S. Department of Defense (DoD) visual information does not imply or constitute DoD endorsement.”




