The Cybersecurity Maturity Model Certification (CMMC) is far from being a one-off effort. On the contrary, CMMC compliance requires continuous monitoring. Keep reading to understand what this means, exactly, and learn more about CMMC.
What Is CMMC Continuous Monitoring?
Continuous monitoring is a concept frequently used in fields such as IT and financial auditing.
However, in the specific context of the Cybersecurity Maturity Model Certification (CMMC), continuous monitoring means maintaining ongoing awareness of a series factors, including:
- Information security
- Vulnerabilities
- Threats
Paying sustained attention to these elements helps support the risk decisions made by an organization.
But in order to fully understand the importance of continuous monitoring, we need to take a step back to review the origins and basic goals of CMMC.
Source: “Cybersecurity Maturity Model Certification (CMMC) Model Overview.” Available online at https://dodcio.defense.gov/
What Is CMMC?
The Cybersecurity Maturity Model Certification is a program designed to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) that is shared with contractors and subcontractors of the Department of Defense (DoD) through acquisition programs.
The CMMC framework has three key features:
- Tiered. CMMC implements cybersecurity standards at progressively advanced levels.
- Assessment requirement. This allows the Department of Defense to verify the implementation of cybersecurity standards.
- Implementation through contracts. Once CMMC is fully implemented, certain DoD contractors that handle sensitive unclassified DoD information will be required to achieve a particular CMMC level as a condition of contract award.
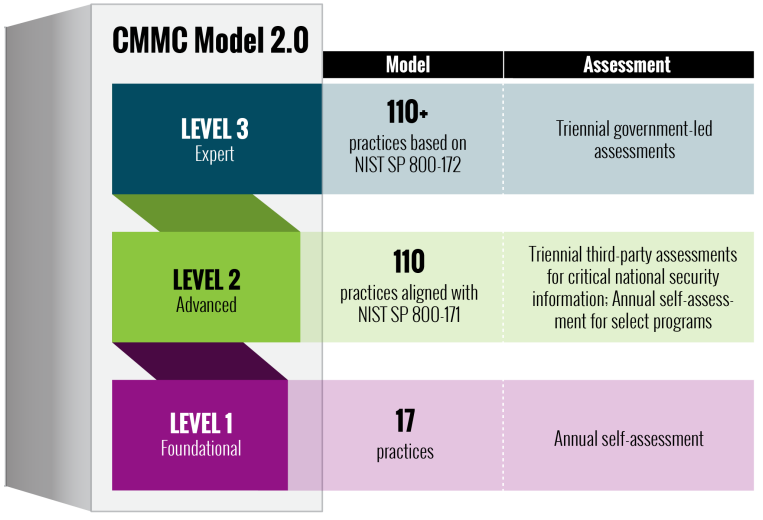
The first iteration of the CMMC program (2020) contemplated five levels, which were subsequently reduced to three in CMMC 2.0 (November 2021):
- Level 1. Foundational: 17 practices, annual self-assessment
- Level 2. Advanced: 110 practices aligned with NIST SP 800-171, triennial third-party assessments for critical national security information; annual self-assessment for select programs
- Level 3. Expert: 110+ practices based on NIST SP 800-172 and 800-17; triennial government-led assessments
Contact Our CMMC Registered Practitioners Today
Why Is Continuous Monitoring Important?
Continuous monitoring is important because threat actors are relentless in both the sophistication and frequency of their attacks. It is only through ongoing awareness that organizations can keep up with the mounting cyberthreats facing the systems and networks used to store, manage, and transmit FCI and CUI.
Once the practices and controls required for CMMC compliance are in place, continuous monitoring helps correct errors in a timely fashion, limit vulnerabilities, and ensure that standards are applied consistently.
Continuous monitoring is carried out through a combination of automated and manual procedures, and includes practices such as:
- Baselining. Monitoring resources to determine typical utilization, making it easier to detect deviations from known patterns.
- Threat Monitoring. Analysis of audit trails and other information collected for the purpose of searching out system events that may constitute violations of system security.
- Vulnerability Management. Identification of vulnerabilities on devices that are likely to be used by attackers to compromise a system.
How CMMC Compliance Can Help
We are a nationwide Registered Provider Organization accredited by the CMMC Cyber AB Board.
Whether it’s CMMC, NIST 800-171, DFARS, or ITAR, we help organizations achieve compliance of all applicable cybersecurity regulations so that they can win and maintain Department of Defense (DoD) contracts. Ready to get started?
Contact our specialists today using the contact form on this website, by phone at (714) 592-0063, or by email at sales@breanetworks.com




